Imagine yourself as a secret agent, tasked with deciphering a message encoded with an intricate system. This message holds the key to a critical mission. You’ve been given tools—a matrix approach—to crack the code, but you’re unsure where to begin. This is the very essence of cryptography, a field where messages are hidden and decoded using mathematical techniques. And in this digital age, the use of matrices for cryptography is more pertinent than ever.
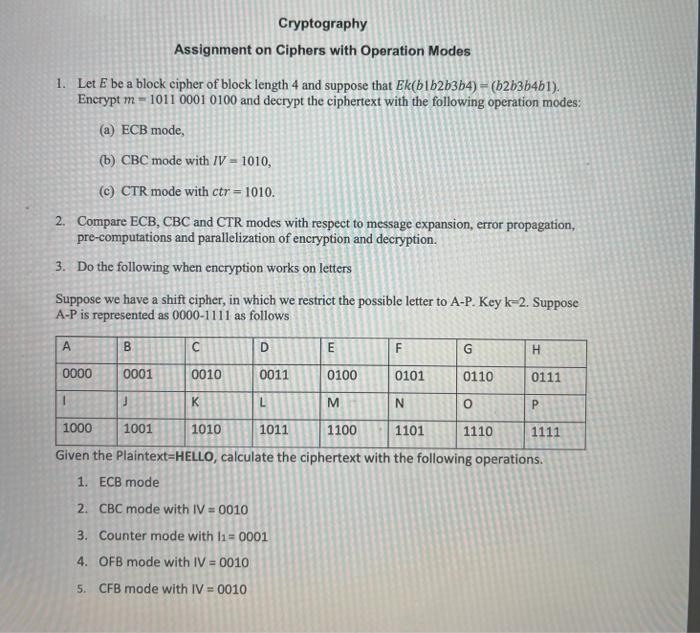
Image: www.chegg.com
Cryptography, with its close ties to mathematics, has long fascinated me. The intrigue of hidden messages and the ingenious methods used to crack them are both captivating and intellectually stimulating. While the world of spies and secret missions might seem far-fetched, the reality is that cryptography plays a vital role in securing our online transactions, protecting our data, and safeguarding our privacy. This article explores the exciting realm of cryptography and how matrices can be employed to break codes, unveiling the hidden messages within.
Understanding Cryptography with Matrices: Decoding the Secrets
What is Cryptography?
Cryptography is the practice and study of techniques for secure communication in the presence of adversaries. Simply put, it’s the art of hiding information so that only the intended recipient can understand it. Cryptography employs various methods to transform plain text, known as “plaintext”, into an unintelligible form called “ciphertext”, making it incomprehensible to unauthorized individuals.
The History of Cryptography
Cryptography has a rich history dating back centuries. Ancient civilizations, including the Egyptians and Romans, used rudimentary forms of cryptography to protect their confidential communications. The famous Caesar cipher, attributed to Julius Caesar, is a simple substitution cipher where each letter in the message is shifted a fixed number of positions down the alphabet. Throughout history, cryptography has evolved, with advancements driven by wars, political intrigue, and technological innovation.
Image: docslib.org
The Importance of Matrices in Modern Cryptography
In modern cryptography, matrices are fundamental tools for encryption and decryption. Their mathematical properties—linearity, reversibility, and the ability to represent complex transformations—make them highly suitable for handling cryptographic operations. Matrices allow the development of robust and secure encryption algorithms that are difficult to break without the correct key.
Deciphering the Code: Using Matrices to Break Cryptography
Matrix Encryption: The Basics
Matrix encryption involves transforming plaintext into ciphertext using a matrix as a key. This transformation typically involves multiplying a matrix representation of the plaintext by the encryption matrix, resulting in a scrambled ciphertext. For instance, each letter of the plaintext can be encoded into a numerical value, creating a vector. This vector is then multiplied by the encryption matrix, producing a ciphertext vector with scrambled values.
Breaking the Code: The Inverse Matrix Approach
To decipher the ciphertext, the intended recipient needs the decryption matrix, which is the inverse of the encryption matrix. The decryption matrix, when multiplied with the ciphertext vector, reverses the scrambling process, leading back to the original plaintext vector. This method hinges on the property of invertible matrices, where a unique inverse exists, allowing for the secure restoration of the original message.
Real-World Applications
Matrix-based cryptography finds applications in encryption protocols used for securing data transmission, authentication, and digital signatures. For instance, public-key cryptography, which relies on pairs of keys—a public key for encryption and a private key for decryption—often employs matrix transformations to ensure secure communication. This method is commonly used in SSL/TLS protocols, protecting online transactions and communication.
The Future of Cryptography: Trends and Innovations
Post-Quantum Cryptography
As quantum computing advances, current cryptographic methods face threats of being broken by powerful quantum algorithms. This has led to the development of post-quantum cryptography, which aims to create encryption algorithms resistant to quantum attacks. Matrix-based cryptosystems are actively researched in this field, leveraging the unique properties of matrices to design secure encryption methods that are less vulnerable to quantum computers.
Homomorphic Encryption
Homomorphic encryption, a novel cryptographic approach, allows computations to be performed directly on encrypted data without requiring decryption, leading to enhanced privacy and security. Matrices play a crucial role in developing efficient homomorphic encryption schemes, enabling secure data processing in various domains, including healthcare, finance, and cloud computing.
Expert Tips for Breaking Cryptography: Decode the Secrets
Understand the Encryption Algorithm
“The first step to breaking a code is to understand the algorithm it uses,” explains Dr. Alan Turing, a renowned mathematician and codebreaker. Identify the type of encryption applied, whether it’s a substitution cipher, a transposition cipher, or a more sophisticated matrix-based method. Knowing the algorithm provides valuable clues for deciphering the message.
Analyze the Ciphertext
Once the algorithm is identified, scrutinize the ciphertext for patterns and redundancies. Look for repeated sequences, common letter combinations, or unusual characters. These anomalies can offer insights into the encryption process and help in identifying the key used. Remember that every ciphertext contains clues, and the ability to decipher them is the key to breaking the code.
Utilize Frequency Analysis
Frequency analysis is a powerful technique used in cryptography to break codes. It involves analyzing the frequencies of letters, symbols, or other elements within the ciphertext. By comparing these frequencies to the expected distribution in the underlying language, it’s possible to deduce possible substitutions or relationships used in the encryption process. With enough frequency data, you can systematically decode the ciphertext.
Frequently Asked Questions
Q: What are some examples of matrix-based encryption algorithms?
A: Examples include Hill cipher, which uses a matrix to encrypt blocks of plaintext, and RSA algorithm, which uses matrices and modular arithmetic to implement public-key cryptography. These algorithms demonstrate the versatility of matrices in cryptography.
Q: Can matrices be used to crack any type of encryption?
A: Matrices are powerful tools for cryptography, but they are not a universal solution. Some modern encryption algorithms, such as AES and Blowfish, employ complex mathematical principles that are not easily cracked using matrix methods alone.
Q: How can I learn more about cryptography and matrices?
A: Online resources, such as Khan Academy and Coursera, offer introductory courses on cryptography and linear algebra. Additionally, books and research papers on cryptography and matrix theory can provide a deeper understanding of the subject.
Cryptography Code Breaker With Matrices Answers
Conclusion: Unlock the Power of Cryptography
Cryptography, particularly the use of matrices, adds a layer of complexity and security to our digital world. From securing sensitive information to protecting online communications, matrices play a pivotal role in safeguarding our data. As the field of cryptography continues to evolve, it’s essential to stay informed about the latest trends and techniques, including the potential use of quantum computers and post-quantum cryptography. By understanding the intricate workings of matrices within cryptography, we can unlock new possibilities for secure communication and protect the data that shapes our digital lives.
Are you fascinated by cryptography and the power of matrices to decode secrets? I encourage you to explore this world further and delve deeper into the mathematical foundations of cryptography. Perhaps you’ll be the next codebreaker, wielding the power of matrices to protect our digital future.





